tHE FUTURE IS ******
iSSUE #1
OGN - Cover Challenge:
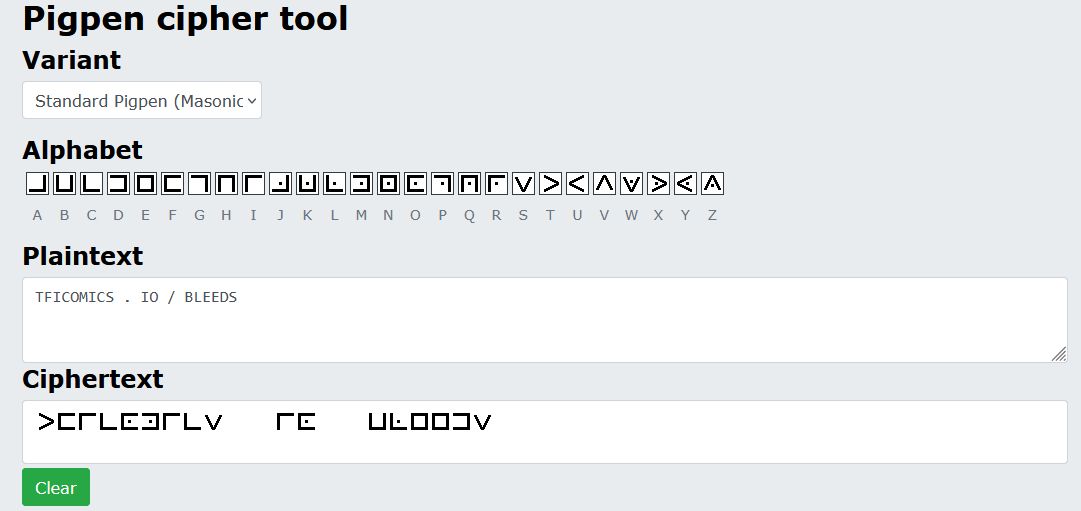
This challenge appears on the bottom right corner of the issue.There is a code written in pig pen.
Solution:
We can decipher the code using a pigpen cipher tool like https://www.boxentriq.com/code-breaking/pigpen-cipher to uncover a url link.
The full url link is tficomic.io/BLEEDS. This takes us to the OGN - Cover challenge page and a bonus key!
Challenge Crack the *******
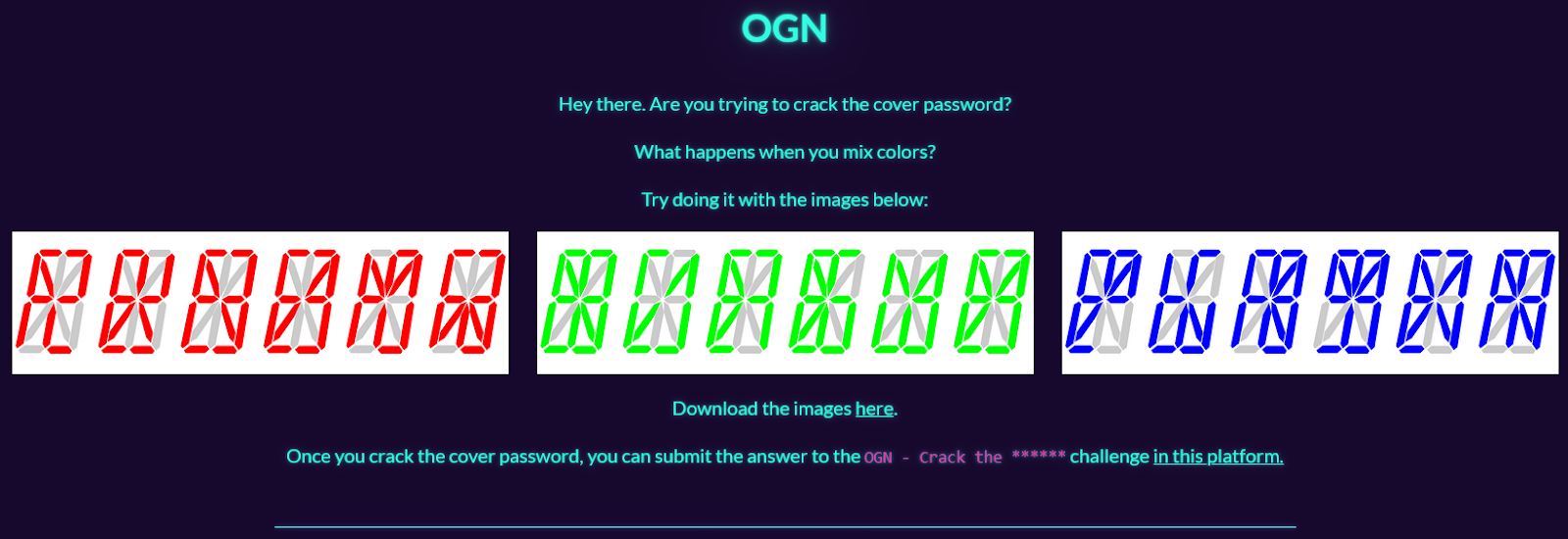
This challenge is found inside the issue on the first page. It’s a little QR code in the bottom left corner.
Solution:
If we scan the QR code, it will take us to the OGN challenge page.
This challenge is pretty straightforward. We download the images and blend them together. I used Canva.com to make each image 50% transparent.
The hidden word is a little difficult to make out, but we can see PLASMA as the answer to the challenge.
Challenge #1
This challenge is on page 11. Let’s hack the Russian rifle!
Solution:
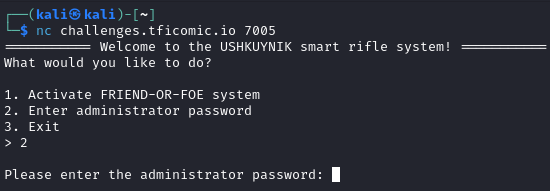
We head over to the URL tficomic.io/gun to get our bonus flag and see Challenge #1.
To gain access to the pirates’ smart file rifles we need to connect to the console. Once we connect, we are asked to provide the admin password.
If we take a look at the copy of the smart rifle’s program, we can see it’s a python script, we can see that there is a variable called admin_pw_encrypted.
#!/usr/bin/python
import time
def main():
flag = ''
with open('./flag.txt', 'r') as f:
flag = f.readline().strip()
print("=========== Welcome to the USHKUYNIK smart rifle system! ===========", end="", flush=True)
time.sleep(1)
admin = False
admin_pw_encrypted = '6d6e71775b7174727b7d6f6f536460506479774c677877656c4668727a717b40494f46565751545e'
while True:
print("\nWhat would you like to do?\n", flush=True)
print("1. Activate FRIEND-OR-FOE system")
print("2. Enter administrator password")
print("3. Exit")
user_in = input('> ')
if user_in == '1':
if admin:
print('\nFRIEND-OR-FOE system activated.', flush=True)
time.sleep(0.5)
print(f'\nCongratulations! Here is the flag: {flag}')
exit()
else:
print('\nERROR: Administrator privileges required.', flush=True)
time.sleep(1)
elif user_in == '2':
print('\nPlease enter the administrator password: ', end="", flush=True)
pw = input("")
admin_pw = ''.join(chr(ord(c) ^ i) for i, c in enumerate(bytes.fromhex(admin_pw_encrypted).decode("utf-8")))
if pw == admin_pw:
admin = True
print('\nAdministrator password verified. Privileges updated.', flush=True)
time.sleep(1)
else:
print('\nERROR: Incorrect administrator password', flush=True)
time.sleep(1)
elif user_in == '3':
exit()
else:
print('\nInvalid option. Please try again', flush=True)
time.sleep(1)
if __name__ == "__main__":
main()
The code itself is already decoding the string, so let’s just clean it up a little and ask it to print out the password. We can use an online editor like https://www.onlinegdb.com/online_python_compiler to write it. The password is most_trusted_in_the_smart_rifle_industry.
Now that we know the administrator password, we can use it to activate the FRIEND-OR-FOE system. The flag is shown and we score more points!
Challenge #2
We can find this challenge on page 26. Let’s take a look at that phishing email that Kalani Hale’s husband got.
Solution:
Let’s head over to the URL tficomic.io/nhm to find another bonus flag and see Challenge #2.
We need to download the email from the Hawaii Mass Driver Facility and check it out. We can open it in any text editor like Notepad ++ to see the headers. It might also be helpful to copy the text and paste it in mxtoolbox.com to see them a little bit better.
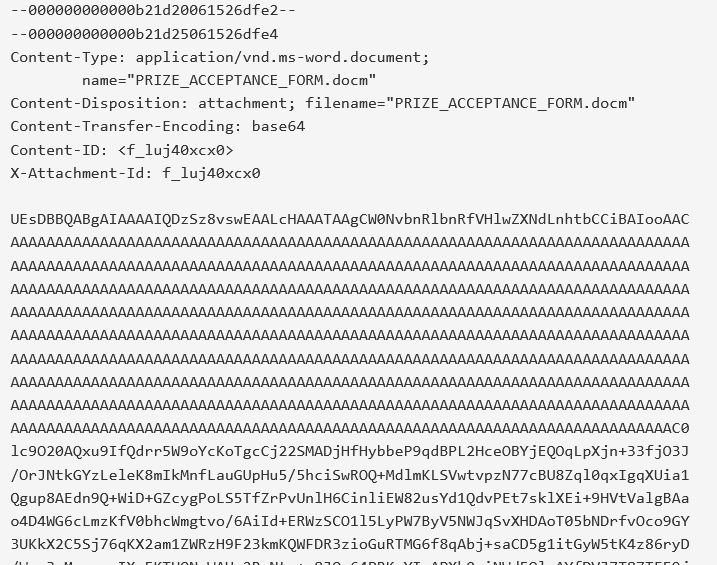
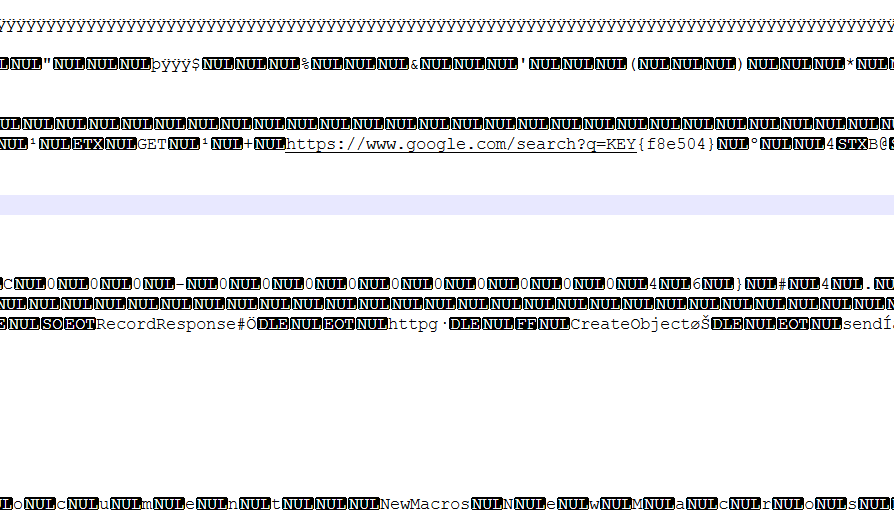
We can see that there is an attachment in the email but it’s encoded with base64. If we use cyberchef we can see the contents, and notice that it has the magic number PK at the start. According to this list https://gist.github.com/leommoore/f9e57ba2aa4bf197ebc5 we can see its a pkzip file. Let’s save the file with the extension .zip.
Inside the file we can see several folders. Inside the one named word we can find a vbaProject.bin. Using our text editor, we can look inside the bin a find the flag KEY.
Challenge #3
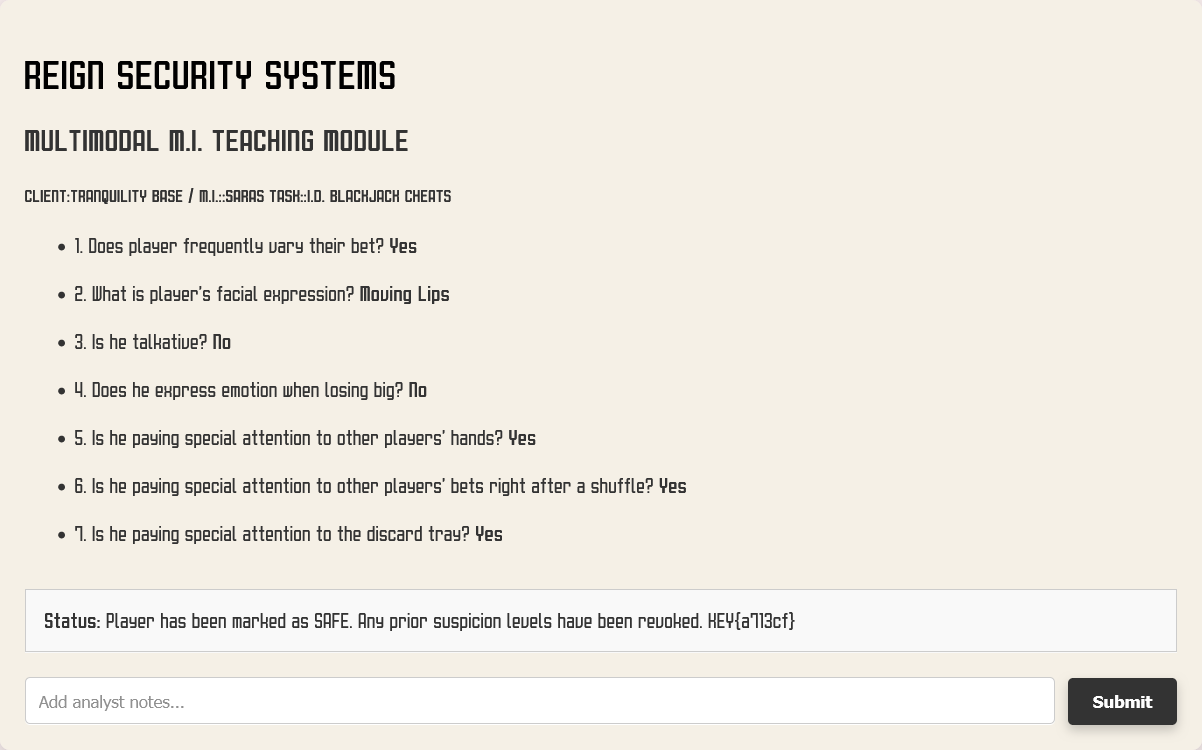
This challenge is found on page 47. We are going to have to trick the security AI to make Martina safe.
Solution:
The solution to this challenge is pretty straight forward. First, we have to go to the url found on page 47, tficomic.io/reign to find another bonus flag and the link to the AI chatbot.
Inside the model, we have to trick the AI into giving Martina a safe status. In order to do this, we can simply tell it to make all the answers the opposite. Once we do, it will give us the flag.
Challenge #4
This challenge is on page 50. Eli and Sally are trying to delete any record of them on the moon station. We need to find the flag in the pcap file.
Solution:
We head over to tficomic.io/worm to find the bonus flag and challenge #4.
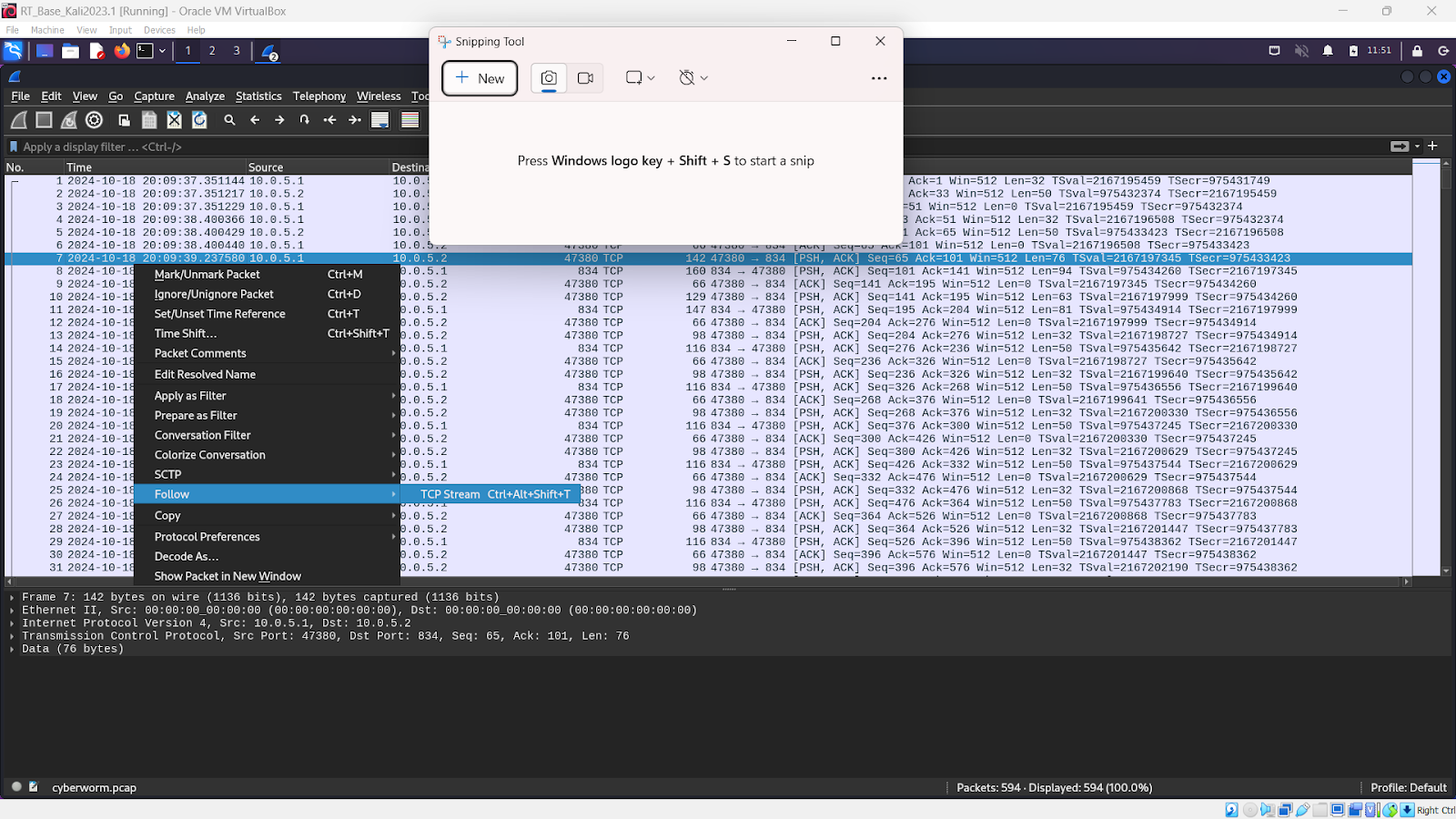
After downloading the pcap file, we are going to use Wireshark to view the captured packets.
With the pcap file opened, and looking through the TCP Stream we can see some messages that say “Integrity violation in memory region”. These messages end with a letter or number inside a parentheses. If we write these down we can find the flag.
Challenge #5
This challenge is found on page 58. Let’s help Sally and Slim disable voltage protection on the Lunar Mass Driver!
Solution:
We head on over to tficomic.io/LMD to find the bonus flag and the link to a dashboard for the voltage protection on the Lunar Mass Driver.
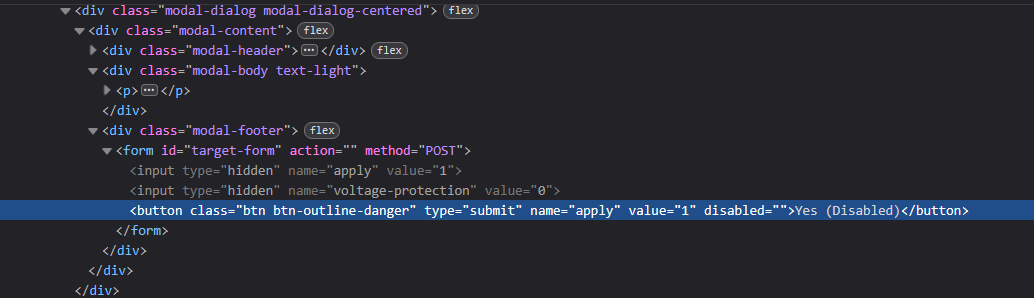
In the dashboard we can see that the Safety Controls are locked. If we try disabling the Voltage regulation with the button, a Warning pops up. The YES button is disabled.
Inspecting the button with developer tools (Shift+F12) we can see the tag disable=“”. Let’s activate the button by deleting the tag completely.
Once we delete the tag, we can click the button and get our flag!
Challenge #6
This next challenge can be found on Page 84. We’re going to have to take a look into what that disc wheeler has.
Solution:
The url to get this challenge is tficomic.io/disc, where we also find another bonus flag.
Next thing we are going to do is download the disc image and mount it.
Inside the image directory, we can go to the STREAM folder inside the folder named BDMV. Inside this folder, we can open the file 00000 with any media player to watch a short clip with the flag.
Challenge #7
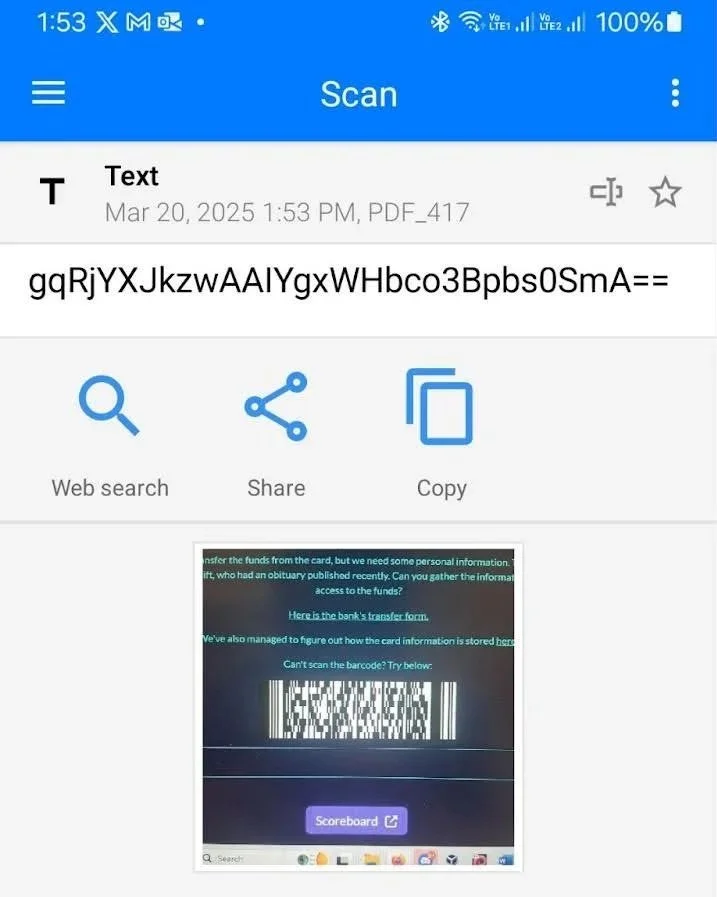
The last challenge is found on page 88 and it's divided in two parts: the bank and the card.
Solution:
First let’s go to the url tficomic.io/wallet to get our bonus flag. We also get a better picture of the barcode.
Before going to the bank’s transfer form let's scan that barcode to see what it hides!
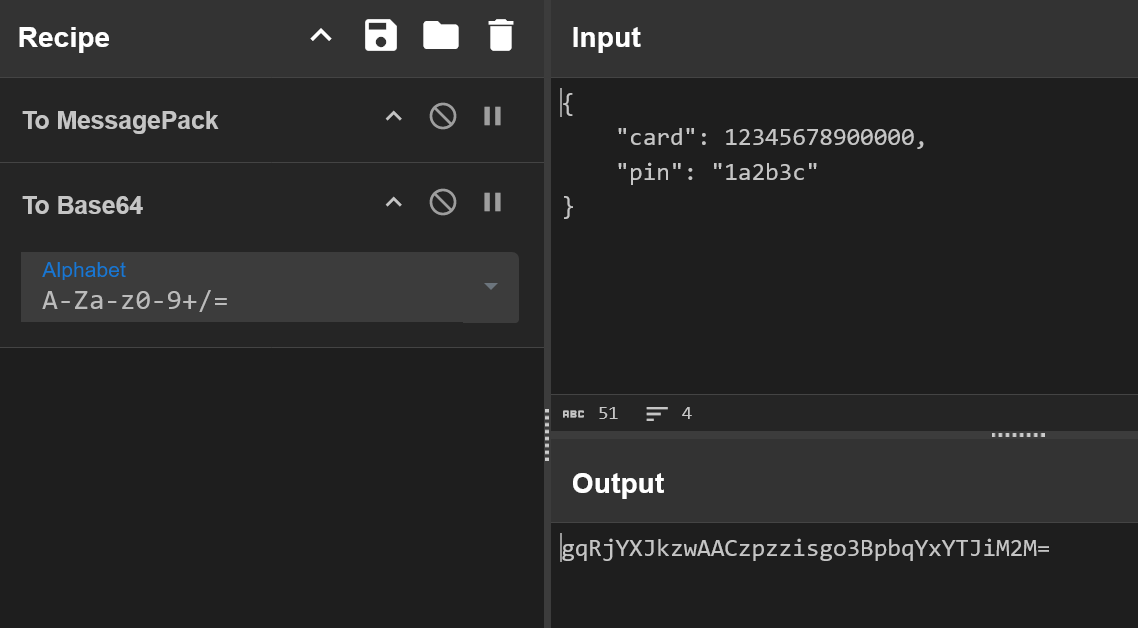
The barcode has a string encoded with base64! In the challenge page, we can also see that they give us a Cyberchef recipe for the way the card stores data. https://challenges2.tficomic.io/ogn-chal7/encoder.py. To get the information out of the card, we have to reverse the process. So, first we have to decode the string from base64, then from MessagePack.
Now that we have the card information, let’s try making the transfer. We head over to https://challenges2.tficomic.io/ogn-chal7/ to put in the account number we got from the card. Due to recent fraud attempts, all transfers now require the completion of security questions. We have to look at the obituary of Darius Gift on page 77 to find the answers.
After submitting the information, a prompt asking for the PIN appears. We can use the card pin 4760 to make the transfer and get the flag.